Download Meraki Vpn Client
The VPN Tracker manual has general configuration instructions. VPN Tracker generally works with the VPN standards IPSec, PPTP & L2TP. There is a free trial for VPN Tracker available, you can easily download the VPN client for Cisco Meraki, it is compatible with all current Apple operating systems. Download the Okta Radius Server Agent Latest Version from your Okta Admin Interface. Settings Downloads Okta Radius Server Agent Download Latest. Enter “Meraki Client VPN” in the. The Meraki MX64 provides unlimited VPN users We love the Cisco Meraki VPN at Telnexus. The MX security appliance is a powerful guardian and gateway between the wild Internet and your private Local Area Network (LAN).
- Cisco Meraki Vpn Client Software Download
- Download Meraki Vpn Client Setup
- Download Meraki Vpn Client Pc
- Configure Meraki Vpn Client
- Cisco Meraki Vpn
The event log can be used to track a number of events occurring across a network. This article describes how to navigate the event log and filter out extraneous information for troubleshooting and monitoring purposes.
Some Meraki VPN client download windows 10 usance tunneling protocols without coding for protecting the privacy of data. Spell VPNs rarely do set security, an unencrypted overlay network does not neatly fit within the secure or trusted categorization.30. .bat and powershell script to create VPN client on Windows machines to connect to Meraki cloud - elramirez3/MerakiClientVPN.

Using the Event Log
Each Meraki network has its own event log, accessible under Network-wide > Monitor > Event log. In a combined network, click the drop-down menu at the top of the page and select the event log for one of the following options:
- for security appliances to display information about the MX security appliance in this network.
- for access points to display information about all MR wireless access points in the network.
- for devices to display information about all managed SM clients in the network.
- for switchesto display information about all MS switches in the network.
- for cameras to display information about all MV cameras in the network.
Note: If a device is offline (and remains powered on), it will continue to gather the information that populates the event log and store it locally. Once the device comes back online, this information will then be uploaded to dashboard with the events keeping their original timestamps.
Filtering the Event Log

While the event log provides a thorough timeline of events on the network, it is usually unnecessary to view all events across all devices. The following options are available to filter down the event log as needed:
Filtering by Client or Cisco Meraki Device
Filtering events to a specific client can help troubleshoot individual connectivity issues, including IP addressing and network authentication. Entering the MAC address, hostname, or custom name in the Client field will display only events affecting that client, excluding other client information and device events.
An additional, product-specific field can be used to filter to events relevant to a specific device in the network. This can be helpful when troubleshooting a particular Meraki device on the network, or a client connected directly to a specific device.
Filtering by Date and Time
Firefox for mac 10.6. The event log shows all events for clients and devices, starting with the most recent event by default. This time frame can be adjusted using the Before field, displaying only events that happened at or before the specified time.
The event log time shares the time zone set for the network itself. More information on changing this time zone can be found here.
Filtering by Event Type
Even when filtering by a single device or client, there can be quite a few events. Selecting specific events to display or excluding specific event types can significantly decrease the amount of data to sort through.
Each Meraki product offers a different variety of reported events, as listed below:
Cisco Meraki Vpn Client Software Download
MX Security Appliance
The following types of events will be reported by MX security appliances:

- Auth: Splash page authentication
- BGP: BGP notification and session events
- Cellular: 3G/4G connectivity
- Client Status: Client connectivity
- DHCP: DHCP leases and related errors
- Events dropped: Too many events were generated too quickly, creating an Events Dropped event
- Filtering: Content filtering blocks
- Intrusion Detection: IDS (Advanced Security only)
- IP conflict: Detected IP conflicts on the network
- Appliance status: Primary uplink events
- Status: Device status events
- OSPF: Events related to OSPF routing
- Route tracking: Route connection change and network test events
- Meraki VPN: AutoVPN connectivity events
- VRRP: Warm spare transition
- Web caching: Web cache events
- Non-Meraki / Client VPN: Non-Meraki and Client VPN connectivity events
- Bad Gateway: Events related to communication issues with the gateway.
- There are two reasons why this event would be logged:
- No_lan_connectivity - The gateway is not responding to ARP requests
- No_inet_connectivity - The Internet and/or DNS connectivity tests are not passing
- Troubleshooting
- Check the physical connection (cables and ports) between the MX and gateway
- Investigate the gateway to determine if traffic is received from the MX
- Confirm that the gateway’s IP and port configuration is correct
- There are two reasons why this event would be logged:
Regarding Bad Gateway events: These events are logged as a result of the Connection Monitoring tests failing. For more information on these tests, please reference the Connection Monitoring article.
MR Access Points
The following types of events will be reported by MR access points:
- 802.11: Wireless association and disassociations
- 802.1X: RADIUS authentication and deauthentications
- Auth: Splash page authentication
- AutoRF: Channel scans and TX power changes
- DFS: Events related to Dynamic Frequency Selection
- DHCP: DHCP leases and related errors
- Events dropped: Too many events were generated too quickly, creating an Events Dropped event
- L3 roaming: Events related to Layer 3 Roaming
- Status: Device status events
- Meraki VPN: VPN tunnel drops and connectivity events
- Air Marshal: Packet floods and wireless security events
- WPA: WPA authentication and deauthentications
Learn more about Common wireless event log messages.
SM Clients
The following types of events will be reported by managed SM clients:
- Command Line: Command line request events
- Live Tools: Recent usage of live tools on client devices
- MDM: Detailed information about changes in device management
- Remote Desktop: Usage of the remote desktop tool
MS Switch

The following types of events will be reported by MS switches:
- 802.1X: RADIUS authentication and deauthentications
- Auth: Splash page authentication
- DHCP: DHCP blocked and no leases available events
- Events dropped: Too many events were generated too quickly, creating an Events Dropped event
- Status: Device status events
- OSPF: Events related to OSPF routing
- Switch port: Port status and STP information
- Switch status: Power and temperature events
- VRRP: Warm spare transition
Learn more about MS event log entries and definitions.
Download Meraki Vpn Client Setup
MV Cameras
The following types of events will be reported by MV cameras:
- Camera: Events related to camera components
- DHCP: DHCP leases and related errors
- Events dropped: Too many events were generated too quickly, creating an Events Dropped event
- Status: Device status events
Posted by: @merakisimon
We’ve all read the horror stories. Passwords, private photos, corporate data, government secrets. What hasn’t been compromised at some point? Connectivity is so important to us that sometimes we forget we may not be the only ones joined to that café hotspot. Thankfully today many of the services we access are reached over an SSL connection, but a Virtual Private Network (VPN) remains the best way to protect all traffic.
Using a VPN in itself is not so hard. An iPhone with VPN configured will simply present a toggle for the user to slide.
So the issue isn’t connecting to VPN, but configuring it in the first place. Even people who consider themselves ‘technical’ can struggle here, because VPN configuration requires the user to configure several settings. Here’s what the iPhone owner is confronted with when attempting to add a new VPN configuration:
Meraki to the rescue! Customers who deploy one of our powerful MX Security Appliances together with Systems Manager have everything they need to build a turnkey VPN solution in their hands. Among the Security Appliance’s many features are comprehensive site-to-site and client VPN. Pairing an MX with Systems Manager adds a number of powerful security features we call Sentry.
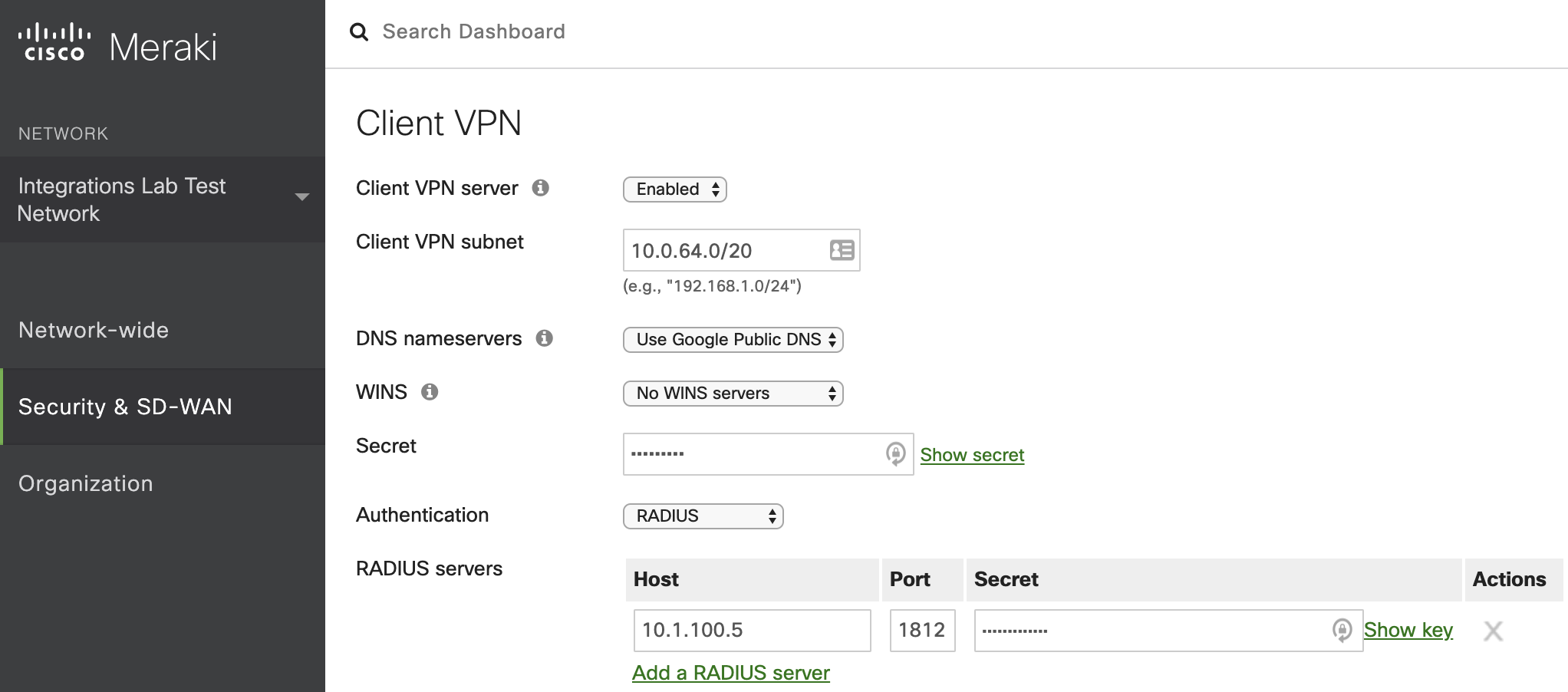
To get things set up, log on to the dashboard and head over to the Client VPN settings page on the MX to which VPN clients will connect. Enable the Client VPN server and then enter the desired settings and then select ‘Systems Manager Sentry VPN Security’. This will open up a new panel as shown here:
Download Meraki Vpn Client Pc
In the Sentry VPN section the admin chooses the Systems Manager network (if there is more than one) and the scope of devices which will receive the VPN settings. The usual Systems Manager tags are available here, both static and dynamic, enabling tight control over which devices will be enabled for VPN. Finally, determine whether this should be a full tunnel VPN (Send All Traffic, a good choice when on unfamiliar networks), and any proxy settings before clicking save. That’s all there is to it! Oh, and we can perform the same trick for Mac OS X too and Samsung Knox enabled Android devices.
Configure Meraki Vpn Client
This truly is simplicity at its best. No need to worry about user configuration, or shared secrets, or server credentials. Everything is automatically pulled from the selected Security Appliance and then pushed out through a profile update to managed clients. The client device will then see the VPN option in settings, and then need only click the toggle to bring the VPN up.
Not ready to purchase a Security Appliance yet? Systems Manager will also allow the manual configuration and deployment of VPN server credentials for any L2TP, PPTP, Cisco IPSec or AnyConnect server.
Sentry is the name we give to a range of security related features which can be used when deploying Systems Manager into an environment with a Meraki network infrastructure. We’ve covered several of these features already on the blog. In this case, Sentry VPN overcomes the biggest obstacle to secure network communications, making it a cinch to set-up, and a trivial option for the end user. Coffee shop productivity just got a lot more secure.
Try Systems Manager on for size by heading over to our website. As with all Meraki solutions, the software is all driven from and accessed via a robust cloud architecture. There’s no hardware required to get started, making it easy to take for a test drive from the comfort of your chair.
Cisco Meraki Vpn
Related Posts
